Top Benefits of Windows 11 IoT Enterprise LTSC – In the ever-evolving landscape of the Internet of Things (IoT), choosing the right operating system is crucial for ensuring seamless device operation, robust security, and long-term stability. Windows 11 IoT Enterprise LTSC emerges as a powerful contender, offering a compelling blend of features specifically designed for the demands of modern IoT deployments.
This comprehensive guide delves into the top benefits of Windows 11 IoT Enterprise LTSC, exploring its unique capabilities and advantages for businesses seeking to leverage the power of IoT.
From enhanced security and stability to tailored features for IoT devices, Windows 11 IoT Enterprise LTSC empowers organizations to build and manage secure, reliable, and efficient IoT ecosystems. This edition offers a distinct advantage over standard Windows 11 releases, providing a dedicated platform for long-term projects and mission-critical applications.
By understanding the benefits of Windows 11 IoT Enterprise LTSC, organizations can unlock the full potential of their IoT initiatives, driving innovation and achieving their business goals.
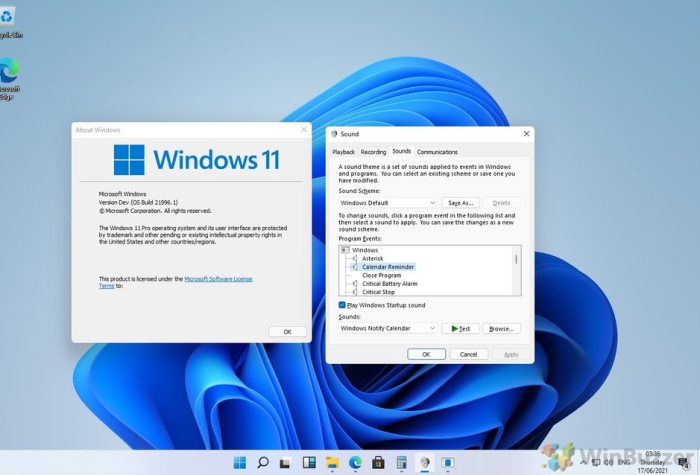
Introduction to Windows 11 IoT Enterprise LTSC
Windows 11 IoT Enterprise LTSC, short for Long-Term Servicing Channel, is a specialized edition of Windows 11 designed for Internet of Things (IoT) devices requiring extended support and predictable updates. It caters to industries and organizations deploying mission-critical IoT applications where stability, security, and long-term support are paramount.
Windows 11 IoT Enterprise LTSC distinguishes itself from other Windows 11 editions by offering a unique blend of features and functionalities specifically tailored for IoT deployments. Unlike the standard Windows 11 releases, which receive regular feature updates, Windows 11 IoT Enterprise LTSC follows a Long-Term Servicing Channel (LTSC) model, providing extended support and predictable updates for a longer period.
Notice Electrical Contractor Software for recommendations and other broad suggestions.
This makes it an ideal choice for scenarios where frequent updates are not desirable or feasible, such as industrial automation, medical devices, and critical infrastructure.
Advantages of Using LTSC for IoT Deployments
The LTSC model offers several advantages for IoT deployments, making it a preferred choice over standard Windows 11 releases.
- Extended Support and Predictability:Windows 11 IoT Enterprise LTSC provides extended support and predictable updates, typically for 10 years, allowing organizations to plan for long-term deployments without worrying about frequent feature updates that could disrupt operations. This long-term support reduces the risk of compatibility issues and ensures continued security updates, making it suitable for mission-critical applications.
- Enhanced Security and Stability:LTSC releases receive security updates and bug fixes for an extended period, ensuring a stable and secure operating environment for critical IoT deployments. This is particularly important for industries like healthcare, where data security and system reliability are of paramount importance.
- Reduced Maintenance Overhead:With a predictable update schedule and extended support, organizations can minimize maintenance overhead associated with frequent updates. This allows IT teams to focus on other critical tasks, reducing operational costs and improving efficiency.
- Optimized for IoT Devices:Windows 11 IoT Enterprise LTSC includes features specifically designed for IoT devices, such as support for various hardware platforms, embedded peripherals, and real-time communication protocols. This makes it easier to integrate with existing IoT infrastructure and develop custom applications tailored to specific needs.
- Customization and Flexibility:LTSC releases offer greater control and customization options for IoT deployments. Organizations can tailor the operating system to their specific requirements, including the ability to remove unnecessary features and applications, reducing the attack surface and improving performance.
Enhanced Security and Stability

Windows 11 IoT Enterprise LTSC is designed to provide a highly secure and stable environment for IoT devices, crucial for deployments where reliability and data protection are paramount. This edition incorporates advanced security features and stability enhancements, making it an ideal choice for mission-critical applications.
Hardware-Based Security
Windows 11 IoT Enterprise LTSC leverages hardware-based security mechanisms to protect devices from unauthorized access and malicious attacks. This includes features like Secure Boot, which ensures that only trusted software is loaded during startup, and TPM (Trusted Platform Module), a dedicated chip that stores cryptographic keys and encrypts sensitive data.
These hardware-based security features provide an additional layer of protection, making it significantly harder for attackers to compromise the device.
Device Lockdown
To further enhance security, Windows 11 IoT Enterprise LTSC allows for strict device lockdown. Administrators can configure device settings to restrict user access, limit application installations, and prevent unauthorized modifications. This lockdown capability is essential for ensuring that devices operate within predefined parameters, reducing the risk of unauthorized access and malicious activity.
Enhanced Threat Protection
Windows 11 IoT Enterprise LTSC includes robust threat protection mechanisms to safeguard devices against malware and other cyber threats. These mechanisms include real-time threat detection, automatic updates, and a comprehensive set of security tools. These features work together to identify and neutralize potential threats, keeping devices safe from malware and other cyber attacks.
Comparison with Other Windows 11 Editions
Compared to other Windows 11 editions, Windows 11 IoT Enterprise LTSC offers enhanced security and stability features specifically tailored for IoT devices. While other editions might provide some security features, they are not as comprehensive or robust as those offered in the LTSC edition.
This makes Windows 11 IoT Enterprise LTSC the preferred choice for deployments requiring the highest levels of security and stability.
Long-Term Support and Reliability: Top Benefits Of Windows 11 IoT Enterprise LTSC
Windows 11 IoT Enterprise LTSC offers a unique advantage for IoT deployments: extended support and reliability. This is achieved through the Long-Term Servicing Channel (LTSC) model, designed to provide stability and predictability for critical systems.
Long-Term Servicing Channel (LTSC)
LTSC is a distinct release channel for Windows that emphasizes stability over frequent feature updates. It offers a fixed set of features and functionality for an extended period, minimizing the risk of compatibility issues and disruptions. This is particularly valuable in IoT deployments, where devices often operate in mission-critical environments with stringent requirements for uninterrupted service.
Extended Support Lifecycle and Predictable Updates
Unlike the regular Windows 11 release cycle, which receives feature updates every six months, LTSC versions are supported for a significantly longer duration, typically 10 years. This extended support lifecycle provides a predictable and stable environment for IoT devices, allowing organizations to plan their deployments and maintenance schedules with confidence.
Real-World Examples of LTSC in Critical IoT Environments
- Industrial Automation:In manufacturing settings, LTSC has been instrumental in ensuring the reliable operation of industrial control systems (ICS). These systems require consistent performance and stability to maintain production lines and minimize downtime. LTSC’s long-term support and predictable updates ensure that these critical systems can operate uninterrupted for extended periods, minimizing the risk of disruptions.
- Healthcare:Hospitals and other healthcare facilities rely on IoT devices for monitoring patients, managing equipment, and optimizing operations. LTSC’s stability and extended support are crucial in these environments, where reliability and security are paramount. The predictable update cycle minimizes the risk of compatibility issues with medical devices and software, ensuring the smooth functioning of critical healthcare systems.
- Smart Cities:Smart city infrastructure relies heavily on IoT devices for traffic management, environmental monitoring, and public safety. LTSC’s long-term support ensures the stability and reliability of these systems, enabling cities to operate efficiently and respond effectively to challenges.
Tailored for IoT Devices
Windows 11 IoT Enterprise LTSC is specifically designed to meet the unique demands of the Internet of Things (IoT) landscape. It offers a robust foundation for building and deploying secure, reliable, and scalable IoT solutions.This version of Windows 11 is tailored for IoT devices by incorporating features and functionalities that cater to the specific requirements of embedded systems and specialized devices.
Support for Diverse Hardware Configurations
Windows 11 IoT Enterprise LTSC supports a wide range of hardware configurations, making it suitable for various IoT applications. It can run on embedded systems with limited resources, as well as on powerful devices with advanced capabilities. This adaptability allows developers to choose the hardware that best suits their specific needs and budget.The operating system is optimized for performance and resource management, ensuring smooth operation even on devices with limited processing power and memory.
It supports various hardware architectures, including x86, ARM, and ARM64, enabling developers to leverage a diverse ecosystem of hardware components.
Customization and Optimization for IoT Use Cases
Windows 11 IoT Enterprise LTSC provides extensive customization options, allowing developers to tailor the operating system to meet the specific requirements of their IoT projects.
Developers can configure the operating system to include only the necessary components, minimizing the footprint and maximizing efficiency.
This granular control over the operating system allows for optimization for specific IoT use cases, such as industrial automation, smart home devices, and retail kiosks.
The LTSC version allows for long-term stability, ensuring that the operating system remains consistent over extended periods, which is crucial for mission-critical IoT deployments.
Simplified Management and Deployment
Windows 11 IoT Enterprise LTSC is designed to streamline management and deployment across large-scale IoT deployments, offering significant advantages over other Windows 11 editions.
Tools and Methods for Management and Deployment
Managing and deploying Windows 11 IoT Enterprise LTSC across a vast network of IoT devices can be challenging. Fortunately, Microsoft provides a range of tools and methods to simplify this process:
- Microsoft Endpoint Manager (MEM):This comprehensive management solution allows you to remotely configure, update, and monitor Windows 11 IoT Enterprise LTSC devices, ensuring consistent security and performance across your entire IoT ecosystem.
- Windows Autopilot:This feature streamlines device provisioning by allowing you to pre-configure devices before deployment, eliminating the need for manual setup and reducing deployment time.
- Group Policy Objects (GPOs):These policies provide granular control over device settings, allowing you to enforce security configurations, software installations, and other essential parameters across your IoT fleet.
- PowerShell:This scripting language enables you to automate repetitive tasks, such as device configuration, software updates, and security policy enforcement, making management more efficient.
Ease of Management and Deployment Compared to Other Windows 11 Editions
Windows 11 IoT Enterprise LTSC offers significant advantages in terms of management and deployment compared to other Windows 11 editions:
- Long-Term Support (LTSC):Unlike other Windows 11 editions that receive frequent feature updates, Windows 11 IoT Enterprise LTSC offers a stable platform with extended support, minimizing the need for frequent re-imaging and configuration changes.
- Simplified Update Management:LTSC provides predictable update cycles, allowing you to plan and schedule updates strategically, reducing the risk of disruptions to your IoT operations.
- Streamlined Device Provisioning:With features like Windows Autopilot and GPOs, Windows 11 IoT Enterprise LTSC enables you to easily configure and deploy devices, reducing the time and effort required for manual setup.
- Centralized Management:Tools like MEM allow you to manage all your Windows 11 IoT Enterprise LTSC devices from a central location, ensuring consistent configurations and policies across your entire IoT deployment.
Cost-Effectiveness and Efficiency
Windows 11 IoT Enterprise LTSC offers a compelling proposition for organizations seeking to optimize their IoT deployments in terms of cost and efficiency. Its long-term support, robust security, and tailored features for IoT devices contribute to significant cost savings and improved operational productivity.
Reduced Maintenance Costs
The extended support lifecycle of Windows 11 IoT Enterprise LTSC eliminates the need for frequent upgrades and associated maintenance costs. This stability ensures consistent device performance and minimizes disruptions, reducing the overall burden on IT resources.
By eliminating the need for frequent software upgrades, organizations can significantly reduce their maintenance costs, freeing up valuable IT resources for other critical tasks.
Extended Device Lifecycles
The long-term support provided by LTSC enables organizations to extend the lifespan of their IoT devices. This is crucial in industries where device replacement can be expensive and disruptive. By maximizing device utilization, organizations can achieve substantial cost savings and optimize their return on investment.
For example, in a manufacturing setting, extending the lifespan of industrial robots or sensors by a few years can translate into significant cost savings, as these devices often represent a significant capital investment.
Minimized Downtime, Top Benefits of Windows 11 IoT Enterprise LTSC
The inherent stability and reliability of Windows 11 IoT Enterprise LTSC minimize the risk of downtime. This is particularly critical in mission-critical IoT deployments where even brief interruptions can have severe consequences. The reduced downtime translates into increased operational efficiency and productivity.
Consider a scenario where a critical sensor in a power plant malfunctions due to software instability. With LTSC, the risk of such disruptions is significantly reduced, ensuring uninterrupted operations and preventing potential financial losses.
Real-World Applications and Use Cases
Windows 11 IoT Enterprise LTSC is not just a theoretical concept; it’s a powerful tool that’s being used to solve real-world problems and drive innovation across various industries. From manufacturing and healthcare to retail and beyond, businesses are leveraging the unique capabilities of LTSC to enhance efficiency, improve security, and gain a competitive edge.
Real-World Examples of Windows 11 IoT Enterprise LTSC Deployment
Here are some examples of how businesses are successfully using Windows 11 IoT Enterprise LTSC to address specific challenges and achieve desired outcomes:
| Industry | Application | Key Benefits Achieved |
|---|---|---|
| Manufacturing | Automated production lines and robotics | Enhanced reliability and stability, reduced downtime, improved operational efficiency, and streamlined management of industrial devices. |
| Healthcare | Medical devices and patient monitoring systems | Increased security and data privacy, extended support lifecycle for critical equipment, and seamless integration with existing healthcare infrastructure. |
| Retail | Point-of-sale systems, digital signage, and inventory management | Improved customer experience, enhanced security for sensitive transactions, and simplified deployment and management of retail devices. |
Final Conclusion
In conclusion, Windows 11 IoT Enterprise LTSC stands as a compelling choice for organizations seeking a secure, stable, and feature-rich operating system for their IoT deployments. Its tailored features, long-term support, simplified management, and cost-effectiveness make it an ideal platform for building and managing secure, reliable, and efficient IoT ecosystems.
As the IoT landscape continues to evolve, Windows 11 IoT Enterprise LTSC empowers organizations to embrace the future of connected devices with confidence, driving innovation and achieving business goals with greater ease and efficiency.
Answers to Common Questions
What are the key differences between Windows 11 IoT Enterprise LTSC and other Windows 11 editions?
Windows 11 IoT Enterprise LTSC is specifically designed for embedded devices and offers extended support, tailored features, and a focus on security and stability. Other Windows 11 editions are primarily aimed at general-purpose computing and receive frequent feature updates.
How does Windows 11 IoT Enterprise LTSC ensure security for IoT devices?
Windows 11 IoT Enterprise LTSC incorporates advanced security features such as hardware-based security, device lockdown, and enhanced threat protection, making it a highly secure platform for IoT deployments.
Is Windows 11 IoT Enterprise LTSC suitable for all types of IoT devices?
Windows 11 IoT Enterprise LTSC is designed for a wide range of embedded devices, including industrial automation systems, medical devices, and retail kiosks. However, specific device compatibility may vary depending on hardware specifications and requirements.
What are some real-world examples of how Windows 11 IoT Enterprise LTSC is being used?
Windows 11 IoT Enterprise LTSC is being deployed in various industries, including manufacturing, healthcare, and retail. For example, it is used to power smart factory systems, medical imaging equipment, and self-checkout kiosks.